|
We want to take this opportunity to inform you that we empower our employees and contractors to obtain COMPTIA certifications such as the Security+. These certifications are not just limited to the workplace environment but can also be applied in everyday life.
The COMPTIA Principles cover a wide range of topics, including security threats, risk management, and incident response. By obtaining these certifications, our employees and contractors are not only enhancing their professional skills but also gaining valuable knowledge that can be used in their personal lives. We believe that investing in our employees' and contractors' professional development is not only beneficial for the company but also for the individuals themselves. We are committed to providing our employees with the resources and support they need to succeed in their careers. Our work principles should not be limited to our professional lives. They should also be a part of our daily lives. When we apply these principles to our personal interactions, we create a more harmonious and productive environment for ourselves and those around us. Let's make a conscious effort to implement these principles in all aspects of our lives. Confidentiality, Integrity, and Availability (CIA) are three important principles of information security that can be applied to everyday life, not just while at work. Let's explore each principle and how it can be used in our daily lives.
By applying the principles of CIA to your everyday life, you can help to protect your personal information and keep it safe.
0 Comments
EvereTech CEO participates in panel about "Importance of Cybersecurity for Small Business"10/28/2021 October 28th 2021, Andrew Everett (EvereTech CEO) served as a panelist in a discussion about the "Importance of Cybersecurity for Small Businesses." The event was hosted by Troy Richardson from the UTSA Small Business Development Center. Cybersecurity experts such as Perry Carpenter (KnowBe4) and Jeff Fair (San Antonio Chamber of Commerce) were also apart of the cyber panel.
EvereTech became a corporate member of CompTIA. This provides employees access to: industry research; employee discounts for training and certifications; networking; communities and councils; events; education and retail discounts. EvereTech is proud to be a corporate member and excited to offer the membership benefits to employees.
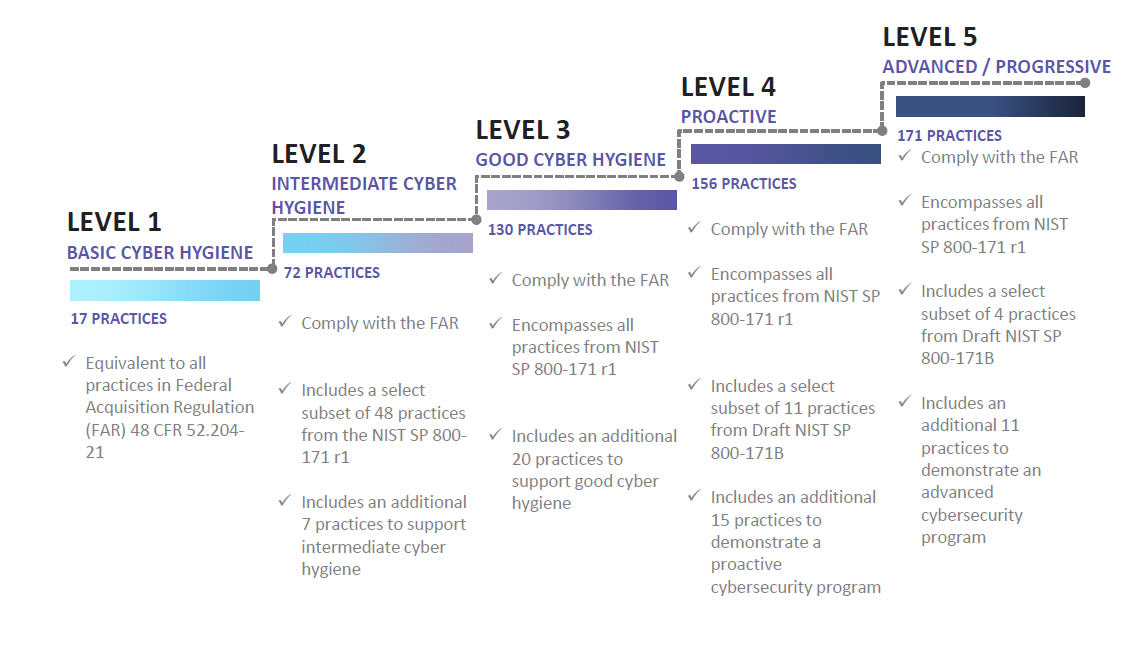
Learn more about CompTIA Here: CompTIA Corporate Webpage  Malicious cyber activity cost the U.S economy between 50-100 billion dollars annually. Impacts can be very substantial when they affect the National Security mission. Malicious actors specifically target the Defense Industrial Base (DIB) (consisting of over 300,000 companies and vendors) as they support the warfighter mission. The Cybersecurity Maturity Model Certification (CMMC), is designed to provide the DOD a verification mechanism designed to ensure that cybersecurity controls and processes adequately to protect Controlled Unclassified Information (CUI) that resides on the Defense Industrial Base (DIB) networks. The DoD expects to include requirements related to CMMC in Requests for Information (RFIs) or Source Sought notices by the summer of 2020. By the Fall of 2020, DoD expects to include specific language in all Requests for Proposals (RFPs). Fortunately, EvereTech is prepared to work with the U.S Department of Defense (DoD) to increase the cybersecurity posture within the multi-tier supply chain including the Cybersecurity Maturity Model Certification (CMMC). We employ the necessary policies and standards to protect the Federal Contract Information (FCI) and Controlled Unclassified Information (CUI). CMMC Maturity Model - GraphicAll information posted was from the Office of the Under Secretary of Defense - Acquisition and Sustainment release that was posted in January 2020. Link listed below.
Additional Resources: https://www.acq.osd.mil/cmmc/draft.html Networks are only as strong as the individuals who use them. When passwords are managed by human defined passwords systems will always remain available for compromise. Passwords are too easy to guess. Additionally, many users repeat passwords and/or PINS across multiple systems allowing increased chances of compromises.
Replacement options for passwords include: iris scanners, fingerprint readers, facial recognition and other authentication factors.
|
Archives
July 2024
Categories
All
|
|
|
Copyright EvereTech LLC | 2024
|








 RSS Feed
RSS Feed